Hacker Reveals How They Faked Accounts and Spent Over 20 Days Stealing Dell Customer Data Without Being Detected
Yesterday Dell confirmed that its website had been hacked, with the stolen data including customers' real names, addresses, and order information, but not financial information, email addresses, or phone numbers.
Although Dell did not disclose the exact number of affected customers, the hacker, @Menelik, revealed on a dark web forum that around 49 million customers were impacted, with the data breach spanning from 2017 to 2024. This means that anyone who purchased products from Dell's website during this period had their data compromised.
In addition, now it seems that Dell's database was not dragged, because the hacker used an unexpected method to obtain the data. It has to be said that the Dell security team is also a grassroots team. The hacker spent more than 20 days crawling the data and was not detected.
Here's how the hacker stole the data:
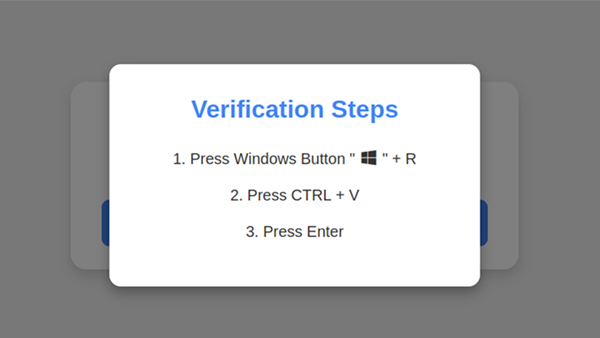
The hacker registered Dell partners under multiple different business names on a specific Dell portal. Such partners are companies that resell Dell products or services. These applications submitted by the hacker were approved by Dell.
The hackers then used these fake partner accounts to forcefully piece together random data and initiate requests (similar to a traversal in a sense) using the customer service tag, which is a unique set of numbers and letters that Dell generates for customers. consists of a 7-digit string.
The permissions Dell has approved for partners include obtaining customers' private information through the customer service label, that is, names, addresses, orders, products or services. This should be Dell's design and not a loophole.
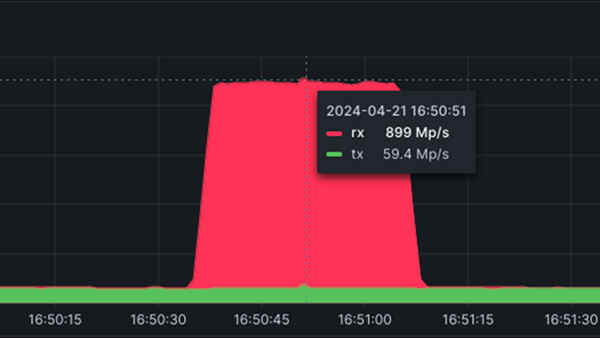
The hackers used multiple different accounts to obtain data from pages containing sensitive customer information at a frequency of 5,000 requests per minute. This work lasted for more than 20 days, and the cumulative number of requests initiated exceeded 50 million.
The Dell security team did notice something during the hacker's operation but didn't seem to deal with it until the hacker thought he had obtained enough data. He stopped the operation and sent multiple emails to Dell notifying Dell of the vulnerability.
In the end, it took Dell a week to fix the vulnerability after receiving the hacker notification, but by then the hackers had obtained enough data to threaten Dell or sell the data for cash.
However, Dell has some slight objections. Dell said that it had noticed the threat and started to fix it before receiving the hacker's email. This is slightly different from the hacker's statement that Dell started to fix it after receiving the notification.
What should be considered a social engineering attack:
This attack can be classified as a social engineering attack, as it involved using fake identities to register accounts and obtain Dell's approval.
In reality, the attack didn't exploit any vulnerabilities in Dell's IT infrastructure, but rather took advantage of the company's weak security configuration, which allowed high-frequency requests to be sent and data to be obtained.
It's likely that Dell didn't anticipate that someone would use randomly generated service tags to steal data, but the problem lies in the fact that Dell's partners didn't need additional approval to access customer private data using these tags.
The entire attack exposed weaknesses in Dell's IT infrastructure, which were caused by human design flaws from the start. Dell's failure to notice these issues ultimately led to the breach.
via @Menelik and TechCrunch