Beware! Phishing Attacks Now Mimic CAPTCHA to Steal Data
Sometimes, the creativity of hackers is simply astounding. They've concocted schemes that trick users into opening Windows Run and executing commands in PowerShell to complete what is presented as a CAPTCHA verification.
This issue was first reported on Github, where, starting from last week, numerous Github users received emails claiming their project codes contained severe security vulnerabilities, with a link provided to view the details.
Upon clicking the link (to the phishing site: hxxps://github-scanner.com), the site would prompt a verification process similar to the Google CAPTCHA system.
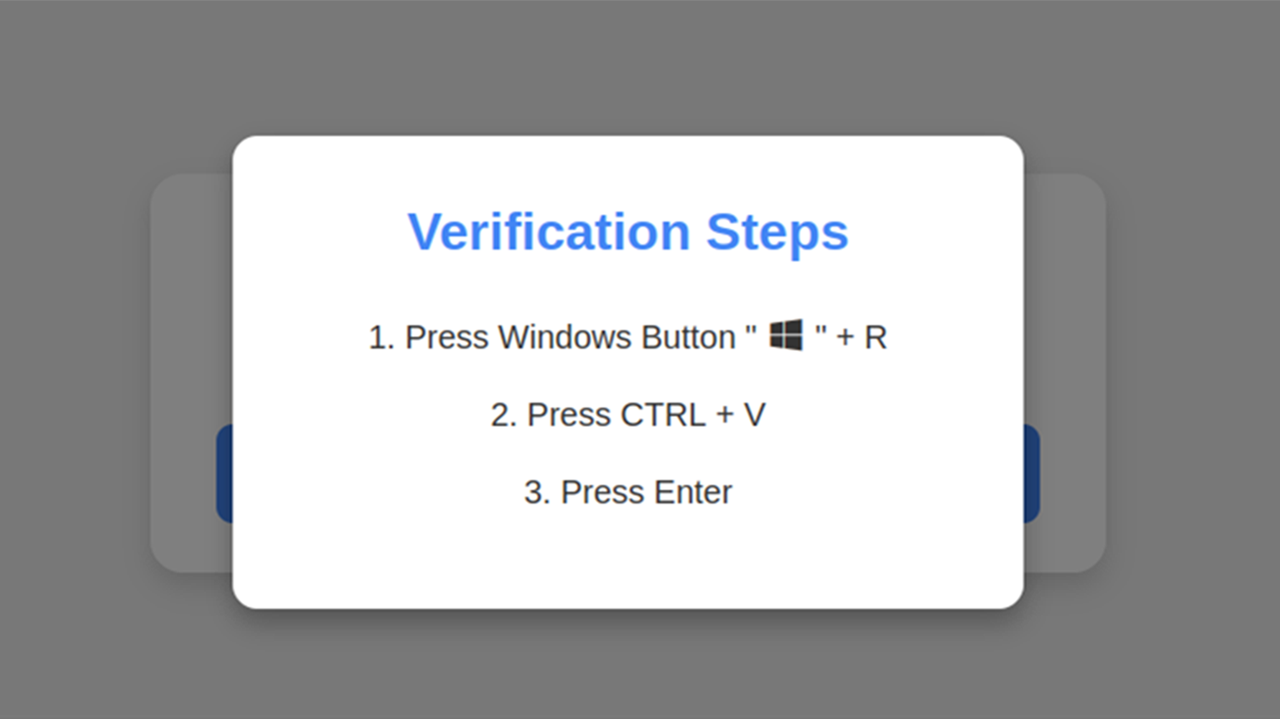
If the user clicks on the "I am not a robot" option, the webpage displays a verification process:
- Press the Windows logo key + R (to open the Run command)
- Press Ctrl+V (at this point, the phishing site's malicious code is already copied to the clipboard, ready to be pasted)
- Press Enter (to execute the malicious code)
In essence, the phishing site hosts malicious code in a script that gets automatically copied to the clipboard when the site is visited. If the user follows through with these steps, they unknowingly execute malicious code within Windows.
This malicious code launches Windows PowerShell to download a file named l6e.exe, which is identified as part of the Lumma Stealer malware family on Virustotal.com.
If executed, this malware can steal various credentials stored on Windows, seemingly with the intent of hijacking the victim's accounts to search for valuable information.
However, the success rate of such phishing tactics is questionable, especially given that many Github users are developers who are likely aware of the potential dangers of executing unfamiliar code via Win+R and Ctrl+V. Hence, this scheme might not have deceived many developers.