Rafel RAT Malware Targeting Android Systems Spreads, Affecting Users in China and the U.S.
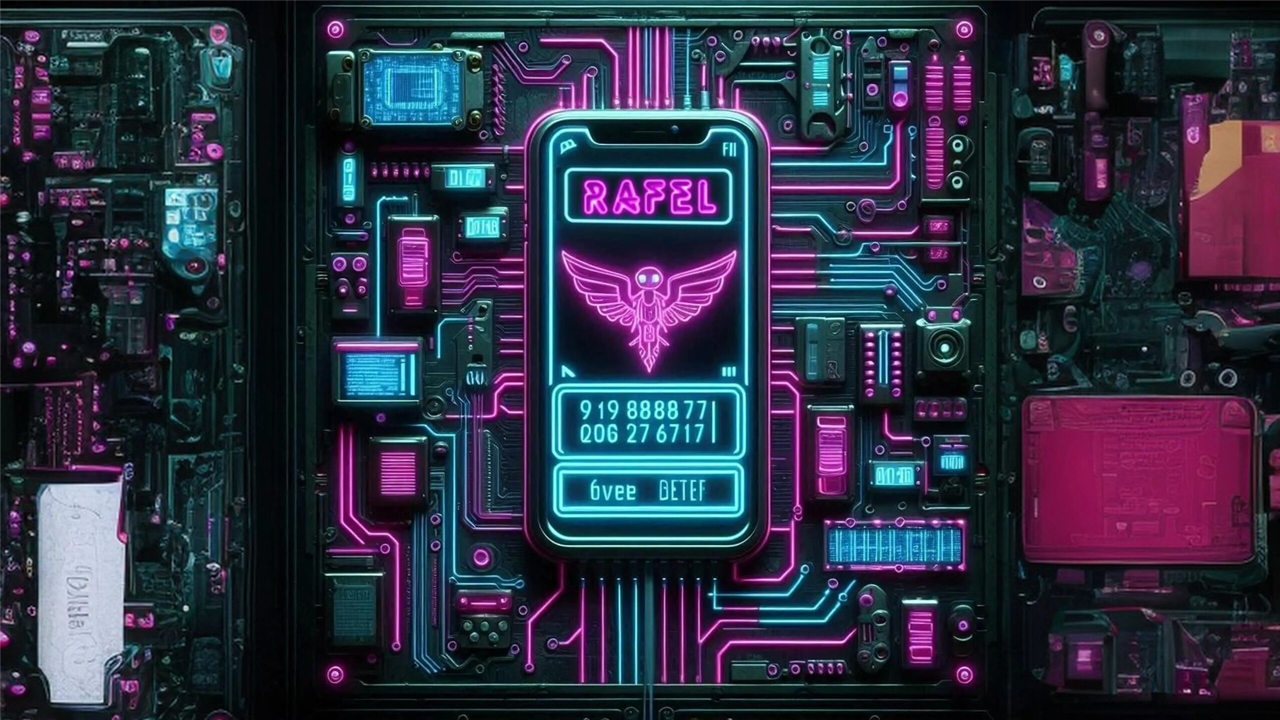
CheckPoint's cybersecurity research team recently revealed a report on the malware known as Rafel RAT. Although not strictly ransomware, Rafel RAT is an open-source malicious software aimed at Android systems, equipped with ransomware-like capabilities to lock files on the user’s device.
The majority of attacked Android devices were found to be running older versions of the Android system, exploiting unpatched security vulnerabilities. Statistics show that over 87.5% of the victims were using Android 11 or older versions.
The advantage of Rafel RAT for hackers lies in its open-source nature and customizability, allowing tailored attacks against various Android device brands, thereby ensuring compatibility with different Android systems customized by OEMs.
Infected devices include brands such as Samsung, Google, Xiaomi, Motorola, OnePlus, Huawei, vivo, etc. The permissions required by different hacker-customized versions of the malware vary, but generally, they request battery optimization permissions to allow the malware to run continuously in the background.
Features of the typical Rafel RAT malware include:
- Ransom functionality: Initiates a file encryption process on the device to encrypt all user data for ransom.
- Wipe command: Enables deletion of all files and folders in a specified path.
- Screen lock: Forces the device screen to lock, preventing the user from unlocking and using the device.
- SMS theft: Steals incoming SMS messages, such as 2FA verification codes.
- Location tracking: Activates location services to collect real-time user location information.
Rafel RAT's ransom functionality uses a hacker-predefined AES key to encrypt files, then changes the screen lock password and displays a custom message asking the victim to contact the hacker via Telegram to pay the ransom for unlocking the device.
If a user attempts to revoke DeviceAdmin privileges, the malware immediately changes the screen password and relocks the screen, forcing the user to either pay the ransom or wipe the device clean.
Implementing ransomware on Android devices is somewhat more challenging compared to Windows PCs, mainly because phones typically do not store as much critical data. Users might opt to simply wipe the device clean instead of paying the ransom.
However, for some users, applications like WeChat do not support cloud sync for chat histories and data. Without prior backups, wiping the phone would result in the loss of all data, which could significantly impact users.
Google has been notified by CheckPoint and is utilizing Google Play Protect to detect and defend against such malicious software, preventing users from installing applications contaminated with Rafel RAT.