Cybersecurity Firm Discovers Hackers Placing Malicious Google Authenticator Ads on Google Search to Steal User Information
Landian.news often criticizes Baidu search for its plethora of junk ads, but Google Search is also rife with similar issues, having been found to host phishing sites and malicious websites through ads on several occasions.
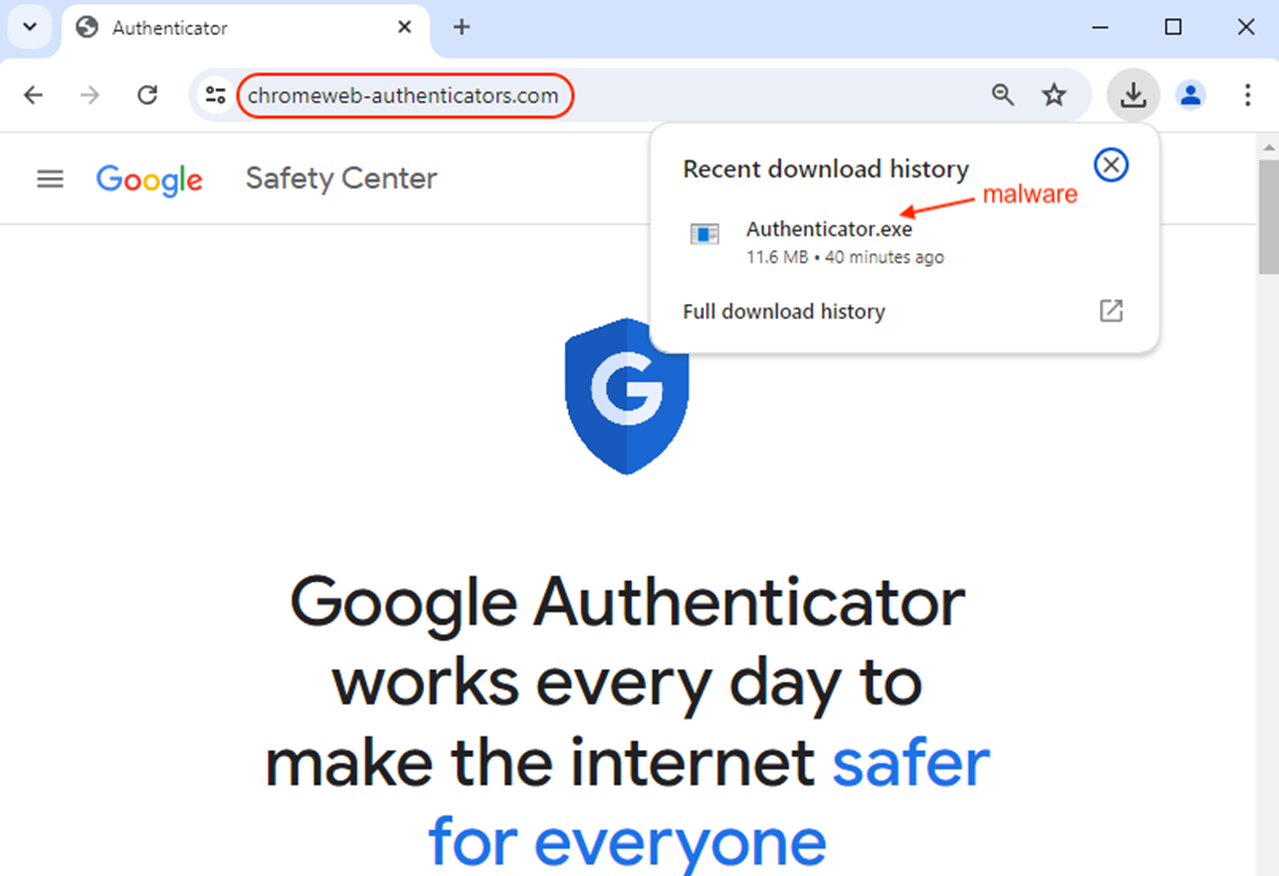
Today, cybersecurity firm Malwarebytes released a new report revealing that Google has allowed hackers to place fake Google Authenticator ads (Google Authenticator), containing malware.
Notably, the hackers managed to bypass Google's ad review mechanism, as the ad appeared to come from google.com and was marked as an authenticated ad provider.
However, clicking on the ad redirects users to a phishing site, chromeweb-authenticators.com, claiming to be the Google Security Center, and prompts users to download a malicious version of Google Authenticator, which is also hosted on GitHub.
When users download it, they are actually getting the installation file from a GitHub project named authe-gogle/authgg, obviously created by the hackers. The hackers also stole a digital signature from a Chinese company, Songyuan Meiying Electronic Products Co., Ltd.to sign the malware. It's unclear whether the digital signature was fraudulently obtained or if Meiying Electronic's digital signature was compromised.
With a legitimate and valid digital signature, when users run the malicious software, the system will not pop up a warning, and some security software might also automatically trust the signed software, potentially compromising security.
Following the report, Google has already taken down the ad, but such incidents are quite common, and it's possible that similar malicious ads are still being placed under other keywords. Therefore, using ad-blocking extensions like uBlock Origin is essential.