Google Chrome v127 Introduces Encrypted Cookie Binding to Prevent Unauthorized Use
The theft and unauthorized use of cookies to access user accounts is a prevalent issue in the digital realm. This process is alarmingly straightforward, particularly when popular browser extensions are acquired by cybercriminal organizations and injected with malicious code designed to steal all cookies saved by the browser. These stolen cookies can then be used to log into user accounts without the need for usernames, passwords, or two-factor authentication (2FA).
In response to this threat, some websites have already implemented more secure strategies. For instance, if the IP address attempting to log in with a cookie differs from the IP address that initially generated the cookie, the attempt is deemed a cookie leak. Consequently, access is denied, and the user is prompted to log in again using their username, password, and 2FA.
Google has recognized the serious threat this method of attack poses to user account security. As a result, the latest Chrome version 127 has introduced encrypted cookie binding. This feature ensures that only the application (website) initiating the login can read and use the cookie, thus preventing its theft by malicious extensions or software.
Will Harris, a Chrome software engineer, shared in a recent blog post that Chrome now utilizes the built-in credential protection features of various operating systems to prevent data theft. These include using KeyChain on macOS, kwallet or gnome-libsecret on Linux, and DPAPI on Windows.
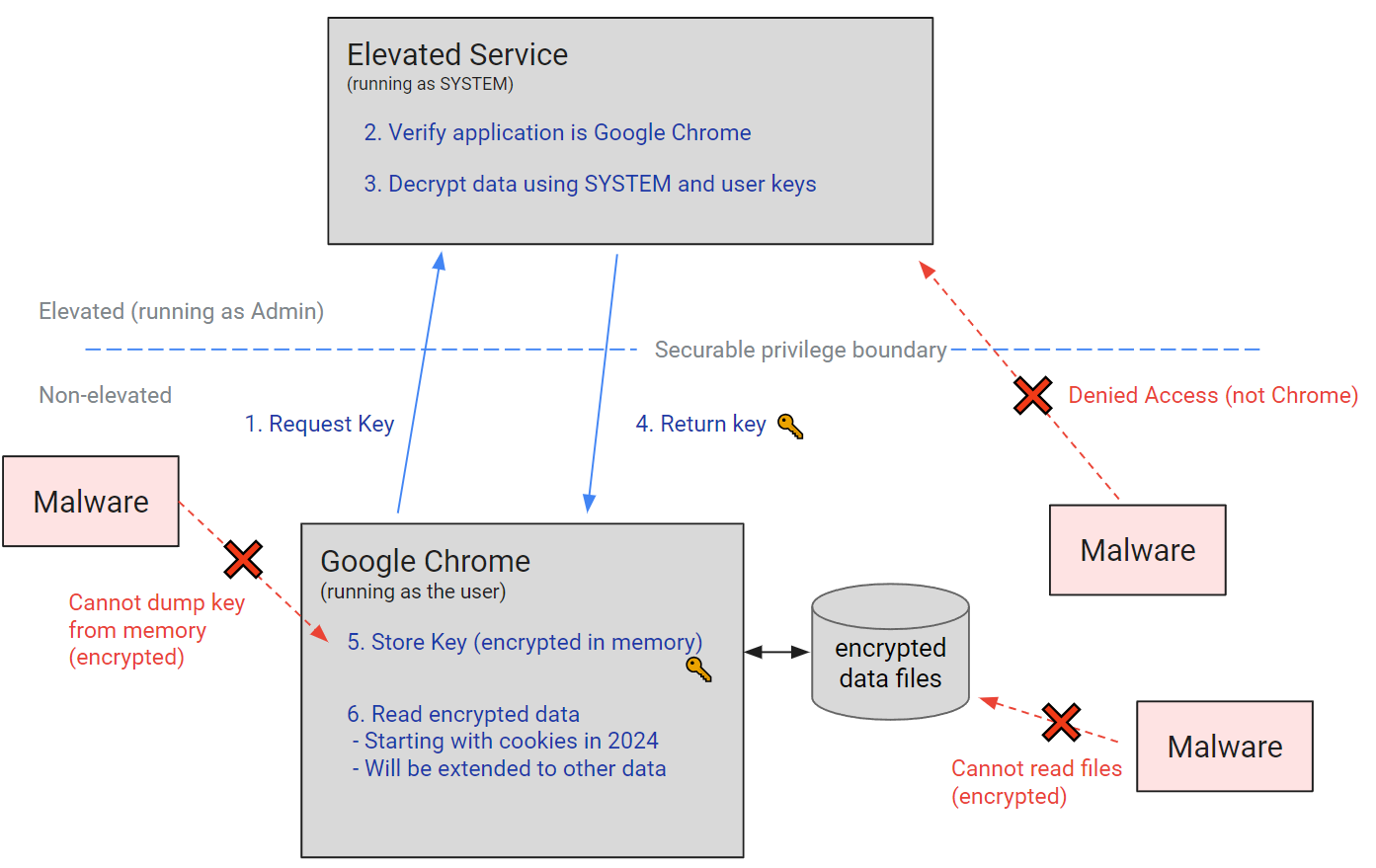
Although the Windows DPAPI protects static data from cold boot attacks, it cannot guard against malicious tools or scripts. Therefore, in Chrome version 127, Google has introduced a new protective measure: Application-bound (App-Bound) encryption primitives to enhance DPAPI.
This app-bound encryption raises the difficulty and cost for attackers trying to steal data, making their malicious activities on the system more conspicuous and easier to detect.
The new protection mechanism operates with Windows SYSTEM privileges for encryption requests. Identity coding, once encrypted, ensures that only the target application can decrypt the data, rendering it unusable by other malicious tools or scripts.
However, to steal data, these malicious tools or scripts would need to obtain system privileges or inject malicious code into the Chrome process—a typical attack vector that security software can easily intercept.
This mechanism is designed not only to protect sensitive data like cookies but also to safeguard user accounts and passwords, payment information, and other persistent authentication tokens from attacks by malicious software.