CA/Browser Forum Considers Disabling WHOIS Verification for Certificate Issuance Due to Its Unreliability
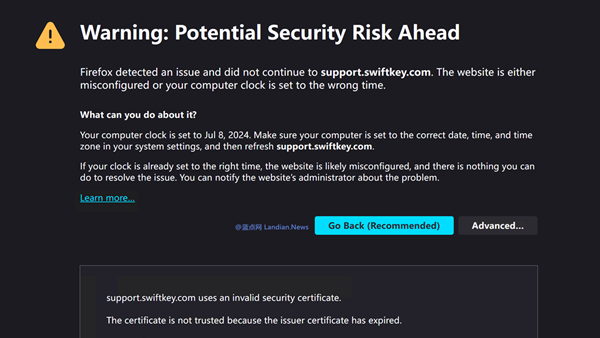
The CA/Browser Forum, responsible for discussing and formulating standards for domain TLS certificates, is currently debating a security flaw discovered by researchers from the security company watchTowr. This flaw allows researchers to obtain TLS certificates for any .MOBI domain.
The flaw itself is relatively straightforward. Several years ago, the CA/Browser Forum established a simplified TLS application mechanism. Under this mechanism, certificate authorities (CAs) would email domain administrators, and clicking a link within the email would be considered confirmation.
Originally, this mechanism, which relies fundamentally on WHOIS information (since the domain administrator's email is listed in the WHOIS database), was meant to simplify certificate management for some administrators. However, its reliance on WHOIS information is where the flaw lies.
The issue identified by watchTowr is specific to .MOBI domains. It arises because the domain registry previously used the official WHOIS website dotmobiregistry.net, which has since been migrated.
After migrating, the need to maintain dotmobiregistry.net diminished, leading to its expiration and subsequent registration by watchTowr. Despite this, various CA organizations continued to treat this site as the official WHOIS server for .MOBI domains.
In this scenario, researchers could spoof the WHOIS server to apply for TLS certificates for any .MOBI domain. Landian.news argues that this scenario doesn't necessarily reflect poorly on the registry but rather on the verification method established by the CA/Browser Forum.
Google has already proposed ceasing the issuance of TLS certificates based on WHOIS information, with a plan to abandon this verification method by early November 2024. However, other CA organizations believe this timeline is too abrupt.
Both Amazon AWS and the renowned CA organization Digicert suggest delaying until the end of April 2025. This delay would provide IT administrators who still use this verification method more time to transition to mainstream verification methods, including file validation and DNS verification.
Additionally, Digicert has proposed replacing WHOIS verification with the RDAP protocol. The RDAP protocol, established by the IETF in 2015 as a successor to the WHOIS protocol, allows for the lookup of registration data from domains, IP addresses, and AS numbers.