CrowdStrike Founder Also Behind Past Blue Screen Incidents, Responsible for the 2010 McAfee Major BSOD Event
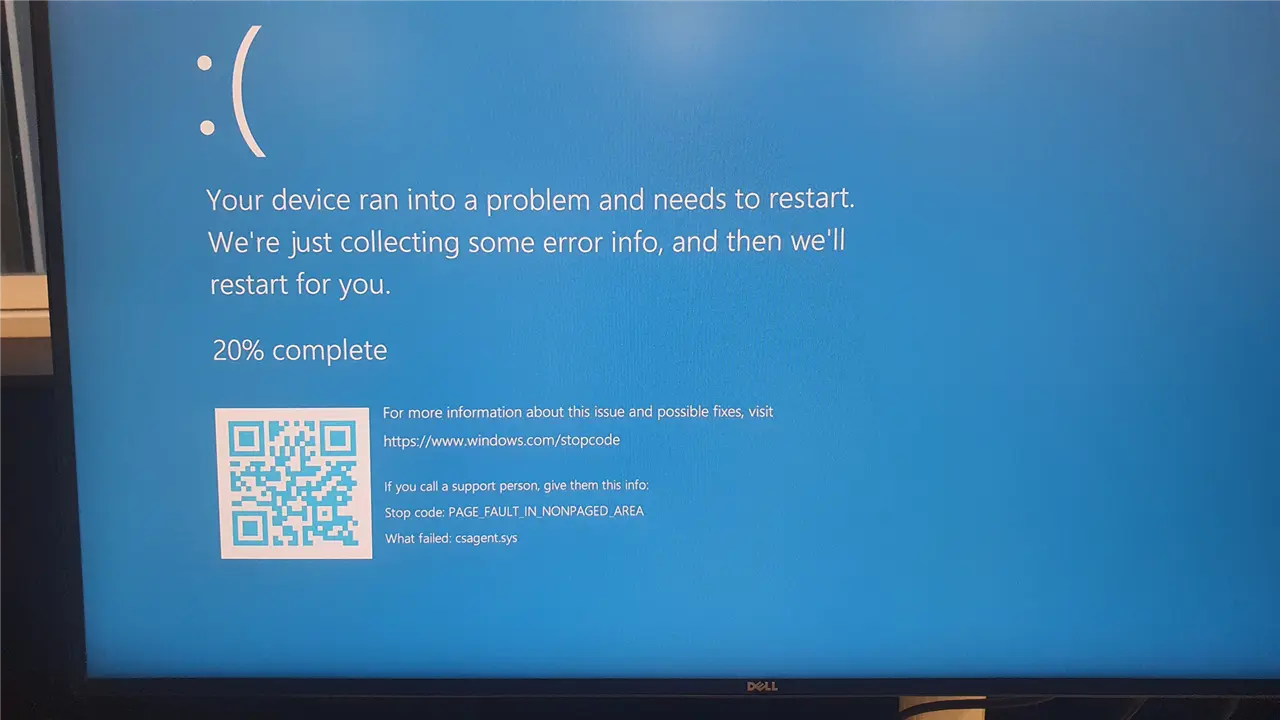
This Friday, a software update released by CrowdStrike led to a blue screen of death (BSOD) on 8.5 million Windows devices worldwide. The potential impact of this event is immeasurable, given that multiple key industries use CrowdStrike's security software.
Unexpectedly, the culprit behind these blue screen incidents seems to be a repeat offender. Internet users have noted that George Kurtz, the founder of CrowdStrike, has been in the cybersecurity field since 2004, serving as Senior Vice President and General Manager of Risk Management at McAfee. In October 2009, he became the Chief Technology Officer of the well-known security software company McAfee, before leaving in October 2011 to establish CrowdStrike, after McAfee was acquired by Intel.
In July 2009, an update to McAfee's virus definition file DAT5664 mistakenly identified multiple legitimate Windows files as viruses and deleted them, primarily affecting Windows XP systems. This deletion of key system files led to BSOD incidents.
In April 2010, another McAfee virus definition update, DAT5958, again mistakenly identified a Windows core file, svchost.exe, as a virus and deleted it, leading to widespread BSOD incidents across Windows XP systems globally.
As McAfee's CTO, George Kurtz was directly responsible for managing these issues. However, McAfee's reputation plummeted after these incidents, and in February 2011, Intel announced its acquisition of McAfee. Kurtz left McAfee in October 2011.
Given that McAfee was the world's second-largest antivirus software at the time, Kurtz should also acknowledge responsibility for its sale to Intel. If he had been more responsible in his role, perhaps so many BSOD issues wouldn't have occurred.
Currently, some professional users on forums are analyzing the cause of this latest CrowdStrike BSOD incident, pointing to issues within the code. However, the key issue seems to be that CrowdStrike released the update without proper testing.
Normally, even simple updates, such as virus definition files, should undergo testing by the development or QA team. Even if no problems are found during testing, updates should be rolled out in stages (e.g., 1%, 5%, 10%, 20%, 50%, 100%) to gradually cover all users, minimizing the impact of any potential issues.
Clearly, CrowdStrike released this update to all customers directly, bypassing both internal testing and phased deployment, which would have easily detected the problem. This represents a significant flaw in the process.
Therefore, while the presence of problematic code leading to BSOD is an issue, the future risk lies in repeating the same mistake if the release process remains unchanged. Future updates could potentially trigger large-scale BSOD incidents again.
This BSOD event has resulted in significant losses for numerous large enterprises worldwide. Since these businesses typically have insurance, some have already begun filing claims with their insurers. However, CrowdStrike may not compensate any customers for their losses.