Bypassing the Guard: The Microsoft Defender Flaw Exposed
Windows has a security mechanism that automatically tags files downloaded from the internet. When a user attempts to open these files, a warning pops up, and users can choose to ignore this warning for the file in its properties.
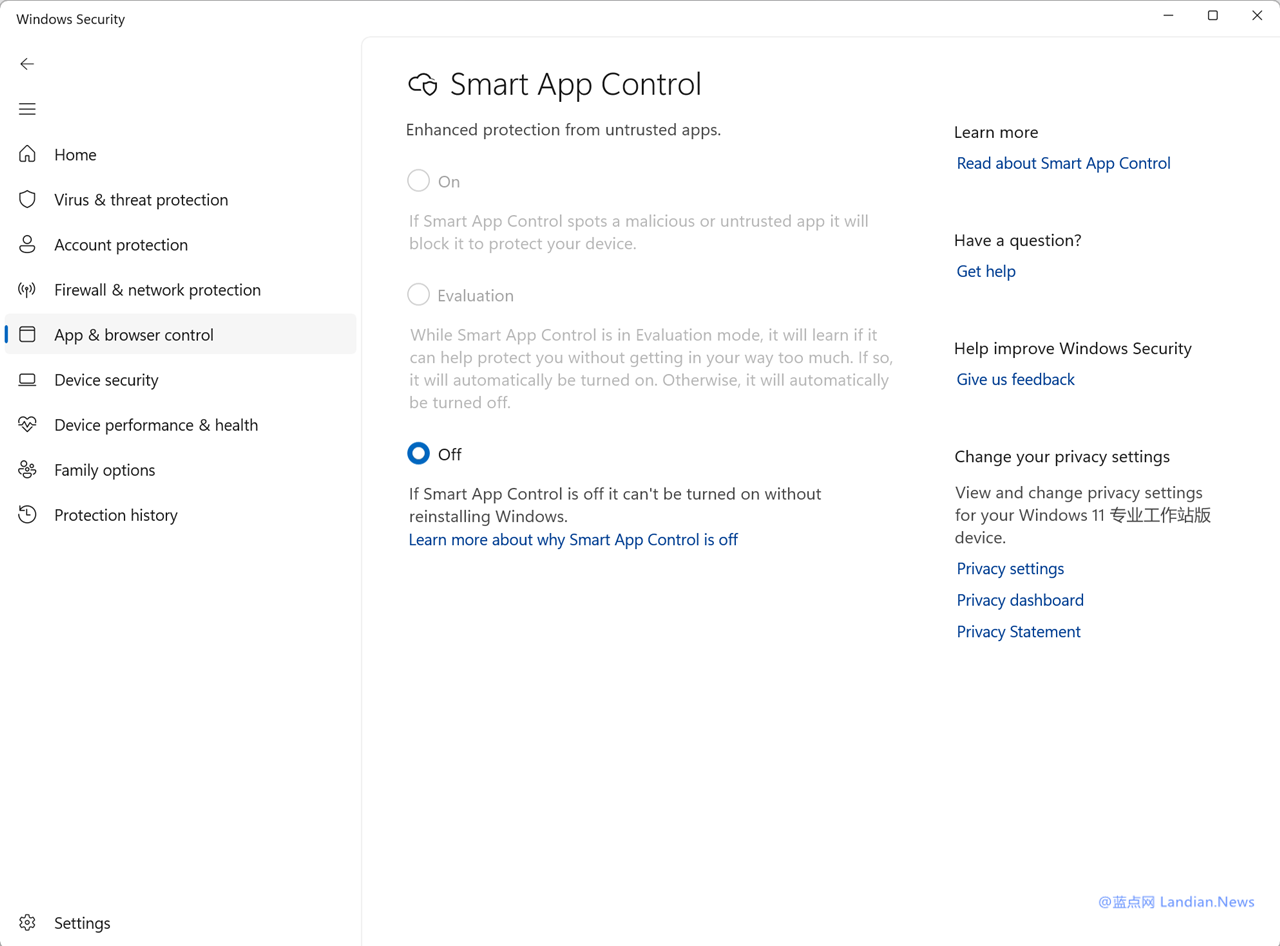
This warning is managed by the SmartScreen filter and the Smart App Control. When a user opens a file downloaded from the internet, both security mechanisms are activated to check the file's safety.
Researchers at Elastic Security Labs have discovered that sometimes Windows Explorer can inadvertently assist in bypassing these protections. For LNK shortcut files, attackers can create LNK files with non-standard target paths or internal structures.
Normally, files that are non-standard or have errors should produce an error message. However, Explorer automatically corrects these issues when a user attempts to open such files. The correction results in the erroneous LNK file being opened, but its tag being removed, meaning it is no longer considered downloaded from the internet.
Since the tag is removed, neither the filter nor Smart App Control is triggered. The process goes like this: a user downloads a hacker-crafted LNK file from the internet and opens it. Explorer instantly corrects and deletes the tag, successfully opening it.
Researchers claim that hackers can bypass these two security checks using this vulnerability. In fact, this flaw has been exploited since 2018, as evidenced by a large number of samples in VirusTotal, with the earliest sample submitted in 2018.
Elastic Security Labs has shared this issue with the Microsoft Security Response Center. Microsoft has stated that it may fix this in future Windows updates, but no specific timeline has been provided.
Researchers warn that users, especially corporate users, should carefully check the security of downloaded content rather than relying solely on the operating system's native security features.